Your Hierarchical attribute based encryption in cloud computing images are ready in this website. Hierarchical attribute based encryption in cloud computing are a topic that is being searched for and liked by netizens today. You can Download the Hierarchical attribute based encryption in cloud computing files here. Find and Download all royalty-free photos and vectors.
If you’re searching for hierarchical attribute based encryption in cloud computing images information connected with to the hierarchical attribute based encryption in cloud computing topic, you have pay a visit to the ideal site. Our website frequently provides you with suggestions for viewing the maximum quality video and picture content, please kindly search and find more informative video articles and graphics that fit your interests.
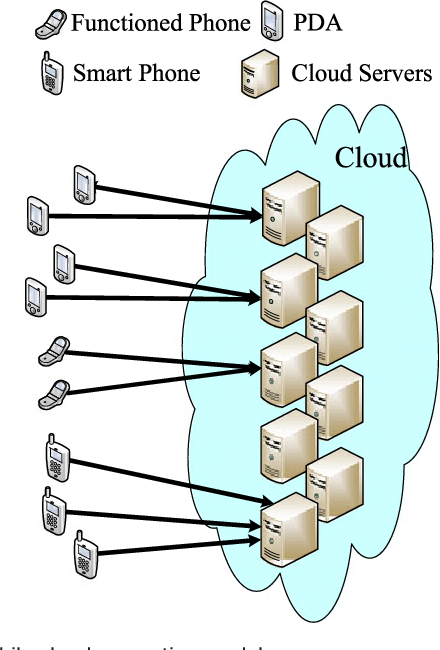
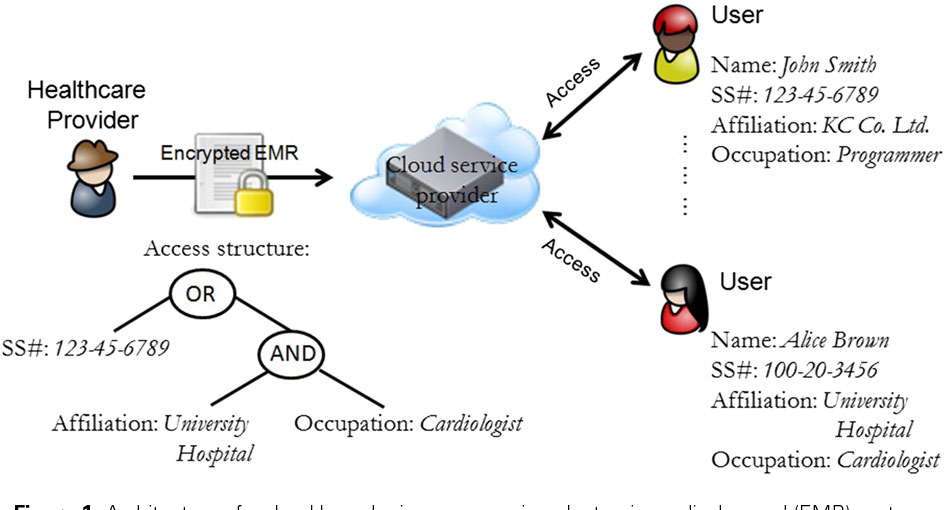
Hierarchical Attribute Based Encryption In Cloud Computing. When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. Based on the proposed CP-ABE algorithm we construct an Attribute-based Hierarchical data Access Control scheme AHAC in the cloud computing. In a specific mobile cloud computing model enormous data which may be from all kinds of mobile devices such as smart phones functioned phones and. By adapting the HABE scheme the performance of public auditing can be improved.
 A Multi Authority Attribute Based Encryption Scheme With Attribute Hierarchy Semantic Scholar From semanticscholar.org
A Multi Authority Attribute Based Encryption Scheme With Attribute Hierarchy Semantic Scholar From semanticscholar.org
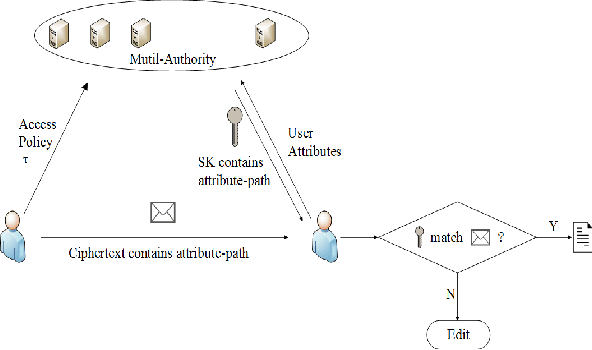
The ciphertext components related to attributes could be shared by the files. The traditional encryption schemes such as symmetric and. HASBE extends the cipher text- prove the security of the proposed scheme based on the policy attribute- set-based encryption CP-ASBE or ASBE. An ancestral node can derive the key of descendants node and every node is. Based on the proposed CP-ABE algorithm we construct an Attribute-based Hierarchical data Access Control scheme AHAC in the cloud computing. In this scheme universal attributes are classified into tree structure according to the relationship defined in the access policy.
The layered access structures are integrated into a single access structure and then the hierarchical files are encrypted with the integrated access structure.
Identify the suitable applications and future direction of attribute based encryption in cloud computing. In this paper an efficient file hierarchy attribute-based encryption scheme is proposed in cloud computing. However storing the data in the untrusted cloud server leads the privacy and access control issues in the cloud. Cloud computing is a revolutionary computing technique by which computing resources are provided dynamically via Internet is widely popular. Cloud computing hierarchical attribute-based encryption fine-grained access control scalability 1. The Hierarchical Attribute Set Based Encryption HASBE to develop a new security feature for various organizational platforms.
 Source: semanticscholar.org
Source: semanticscholar.org
When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. Its an emerging but promising paradigm to integrating mobile devices into cloud computing and the integration. However storing the data in the untrusted cloud server leads the privacy and access control issues in the cloud. In addition it provides. It is implemented using cipher text policy by encrypting and decrypting the data in the cloud so that the cloud system becomes more scalable and flexible by.
 Source: semanticscholar.org
Source: semanticscholar.org
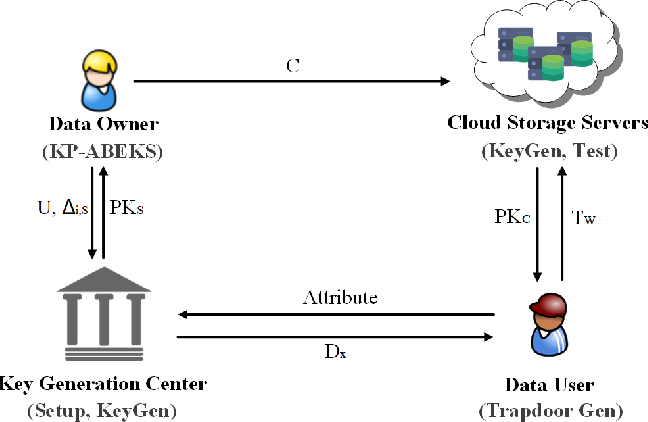
Cloud computing is one of the emerging technology of IT industry in recent times. Encryption CP-ABE and Key-Policy Attribute-Based Encryption KP-ABE. In order to achieve scalable fine-grained and flexible access control for cloud computing we extends Ciphertext-Policy Attribute-Set-Based Encryption CP-ASBE by building in a hierarchical structure to obtain Hierarchical Attribute-Set-Based Encryption HASBE for cloud computing. In this paper an efficient file hierarchy attribute-based encryption scheme is proposed in cloud computing. Its an emerging but promising paradigm to integrating mobile devices into cloud computing and the integration.
 Source: mdpi.com
Source: mdpi.com
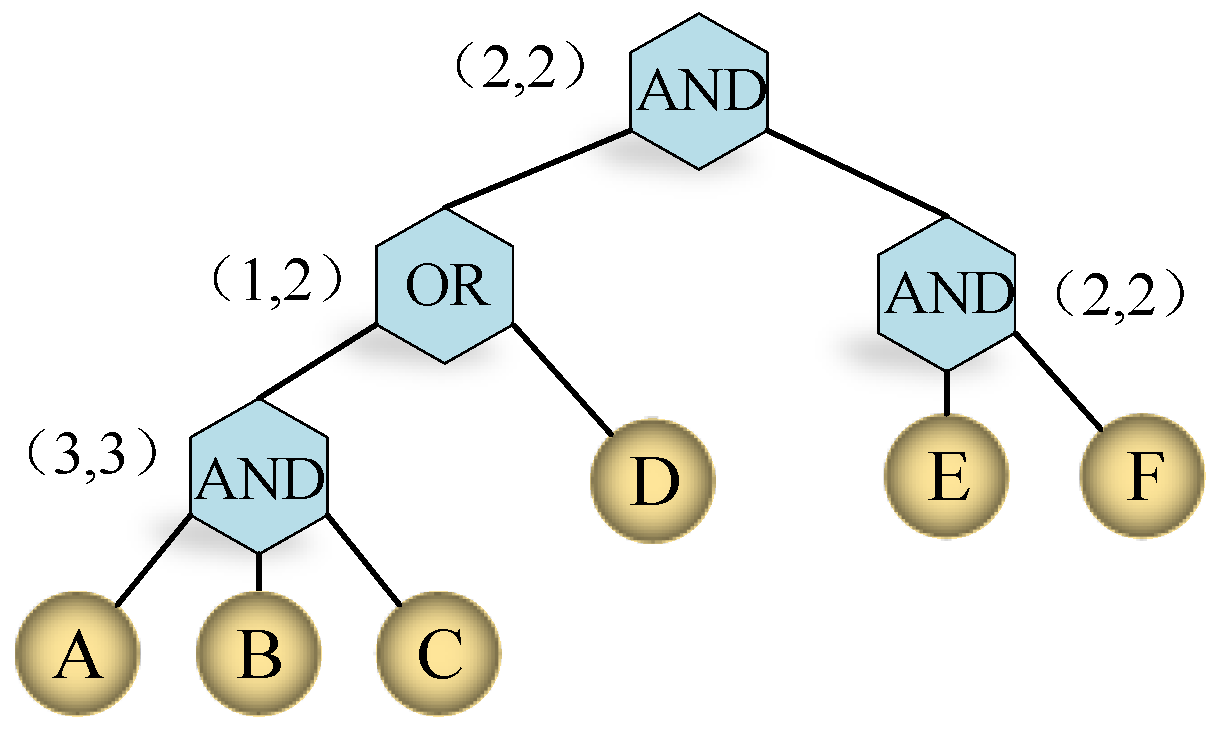
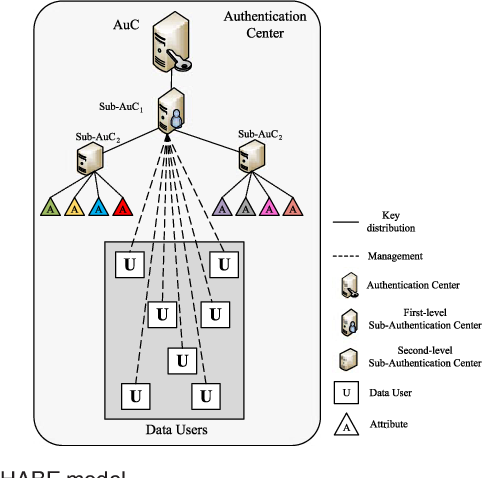
These techniques suffer from problems in implementing flexible and scalable access control mechanisms. Cloud computing is an Internet-based computing pattern through which shared resources are provided to devices on demand. Introduction With the widespread applications of network technology and the global rise of cloud technology cloud computing is rapidly evolving to revolutionize the way how service is. In this paper a hierarchical attribute driven role based access control system is proposed such that the user role assignments can be automatically constructed using policies applied on the attributes of users and roles. The hierarchical attribute based encryption ABE is the scheme which splits the entire data into different levels and the user can access only the specified level of data.
 Source: researchgate.net
Source: researchgate.net
Cloud computing is an Internet-based computing pattern through which shared resources are provided to devices on demand. The layered access structures are integrated into a single access structure and then the hierarchical files are encrypted with the integrated access structure. INTRODUCTION With the emergence of sharing confidential corporate data on cloud servers it is imperative to adopt an efficient encryp-Copyright is held by the authorowners. In order to achieve scalable fine-grained and flexible access control for cloud computing we extends Ciphertext-Policy Attribute-Set-Based Encryption CP-ASBE by building in a hierarchical structure to obtain Hierarchical Attribute-Set-Based Encryption HASBE for cloud computing. Cloud computing is an Internet-based computing pattern through which shared resources are provided to devices on demand.
 Source: semanticscholar.org
Source: semanticscholar.org
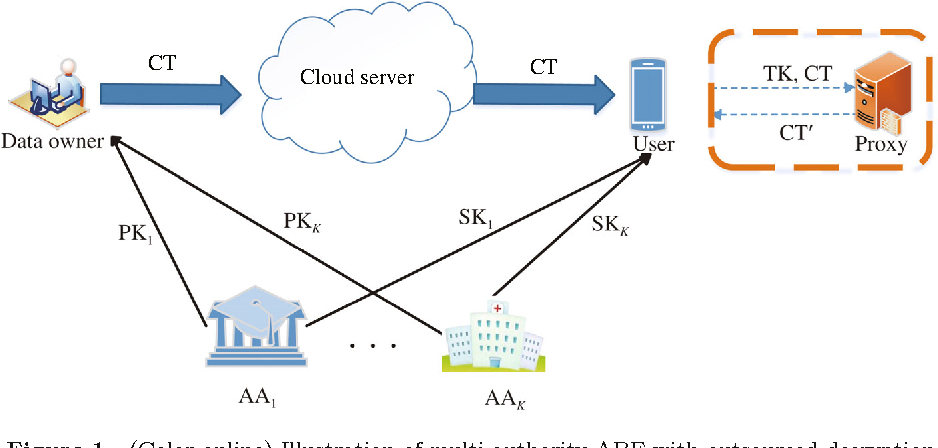
Hierarchical attribute based proxy re-encryption access control in cloud computing Abstract. In a specific mobile cloud computing model enormous data which may be from all kinds of mobile devices such as smart phones functioned phones and. The HABE model which incorporates the property of hierarchical generation of keys in the HIBE system and the property of flexible access control in the CP-ABE system is more applicable to the. The proposed access control system consequently solves the scalability and key management problems in cloud storage systems. The layered access structures are integrated into a single access structure and then the hierarchical files are encrypted with the integrated access structure.
 Source: link.springer.com
Source: link.springer.com
The traditional encryption schemes such as symmetric and. In this paper a hierarchical attribute driven role based access control system is proposed such that the user role assignments can be automatically constructed using policies applied on the attributes of users and roles. In this scheme universal attributes are classified into tree structure according to the relationship defined in the access policy. Cloud computing is a revolutionary computing technique by which computing resources are provided dynamically via Internet is widely popular. Cloud computing is one of the emerging technology of IT industry in recent times.
 Source: researchgate.net
Source: researchgate.net
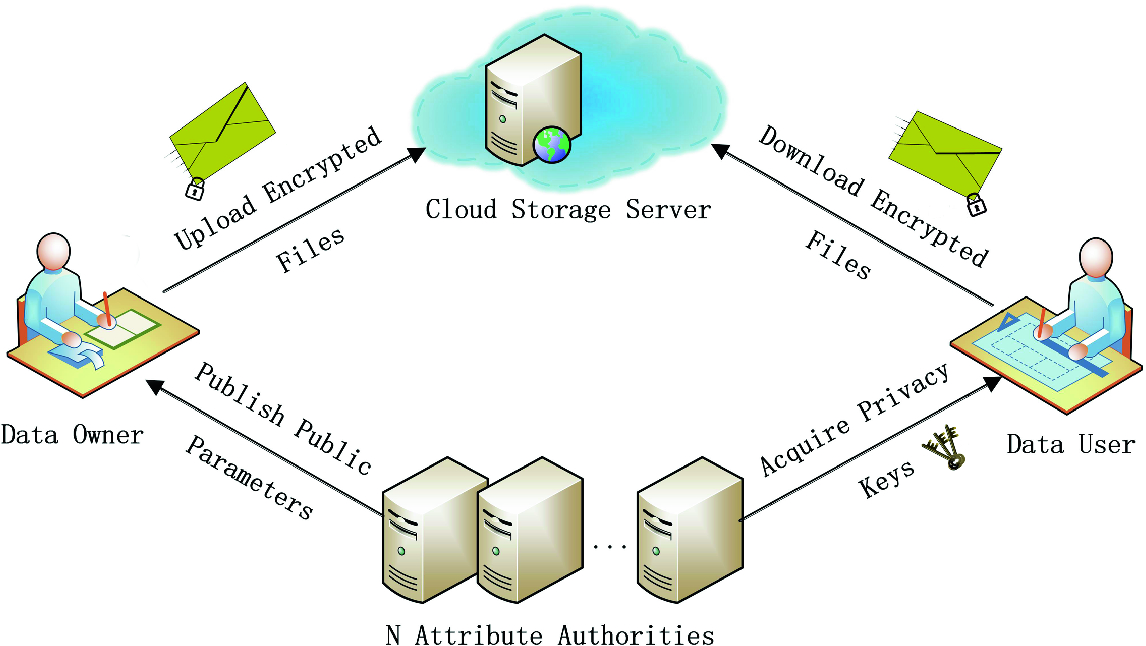
Cloud computing is one of the emerging technology of IT industry in recent times. A Practical Attribute-Based Document Collection Hierarchical Encryption Scheme in Cloud Computing AbstractCiphertext-policy attribute-based encryption can provide fine-grained access control and secure data sharing to the data users in cloud computing. A Modified Hierarchical Attribute-Based Encryption Access Control Method for Mobile Cloud Computing ABSTRACT. The hierarchical attribute based encryption ABE is the scheme which splits the entire data into different levels and the user can access only the specified level of data. The ciphertext components related to attributes could be shared by the files.
 Source: semanticscholar.org
Source: semanticscholar.org
In addition it provides. The traditional encryption schemes such as symmetric and. In order to provide safe and secure operation a hierarchical access control method using modified hierarchical attribute-based encryption M-HABE and a modified three-layer structure is proposed in this paper. Encryption CP-ABE and Key-Policy Attribute-Based Encryption KP-ABE. Identify the suitable applications and future direction of attribute based encryption in cloud computing.
 Source: researchgate.net
Source: researchgate.net
The proposed scheme inherits flexibility in supporting compound attributes. The ciphertext components related to attributes could be shared by the files. On outsourced data it provides both efficient and flexible access control in cloud computing. This new technology requires entrust the users valuable data to the cloud server since this cloud computing have the major disadvantage over security and privacy to the outsourced data to. A Modified Hierarchical Attribute-Based Encryption Access Control Method for Mobile Cloud Computing ABSTRACT.
 Source: semanticscholar.org
Source: semanticscholar.org
By adapting the HABE scheme the performance of public auditing can be improved. In order to provide safe and secure operation a hierarchical access control method using modified hierarchical attribute-based encryption M-HABE and a modified three-layer structure is proposed in this paper. Since the most attractive part of clo. The ciphertext components related to attributes could be shared by the files. A Survey on Hierarchical Attribute Set based Encryption HASBE Access Control Model for Cloud Computing Vanraj Kamliya Research Scholar Department of CE.
 Source: link.springer.com
Source: link.springer.com
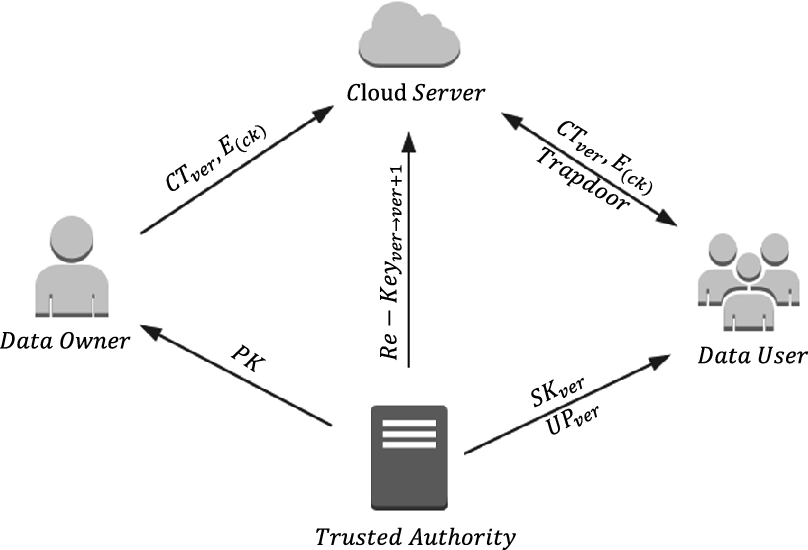
The layered access structures are integrated into a single access structure and then the hierarchical files are encrypted with the integrated access structure. When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. INTRODUCTION With the emergence of sharing confidential corporate data on cloud servers it is imperative to adopt an efficient encryp-Copyright is held by the authorowners. A Modified Hierarchical Attribute-Based Encryption Access Control Method for Mobile Cloud Computing Yuanpeng Xie Hong Wen Bin Wu Yixin Jiang and Jiaxiao Meng AbstractCloud computing is an Internet-based computing pattern through which shared resources are provided to devices on-demand. Cloud computing is a revolutionary computing technique by which computing resources are provided dynamically via Internet is widely popular.
 Source: semanticscholar.org
Source: semanticscholar.org
Even the user gets the entire data he can extract the original information if he posses the specified key. This paper provides Hierarchical Attribute-Based Solution in cloud environment. The proposed scheme inherits flexibility in supporting compound attributes. Encryption CP-ABE and Key-Policy Attribute-Based Encryption KP-ABE. The HABE model which incorporates the property of hierarchical generation of keys in the HIBE system and the property of flexible access control in the CP-ABE system is more applicable to the.
 Source: researchgate.net
Source: researchgate.net
HASBE extends the cipher text- prove the security of the proposed scheme based on the policy attribute- set-based encryption CP-ASBE or ASBE. In this paper an efficient file hierarchy attribute-based encryption scheme is proposed in cloud computing. The layered access structures are integrated into a single access structure and then the hierarchical files are encrypted with the integrated access structure. Its an emerging but promising paradigm to integrating mobile devices. The traditional encryption schemes such as symmetric and.
 Source: mdpi.com
Source: mdpi.com
An ancestral node can derive the key of descendants node and every node is. The layered access structures are integrated into a. The ciphertext components related to attributes could be shared by the files. The ciphertext components related to attributes could be shared by the files. INTRODUCTION With the emergence of sharing confidential corporate data on cloud servers it is imperative to adopt an efficient encryp-Copyright is held by the authorowners.

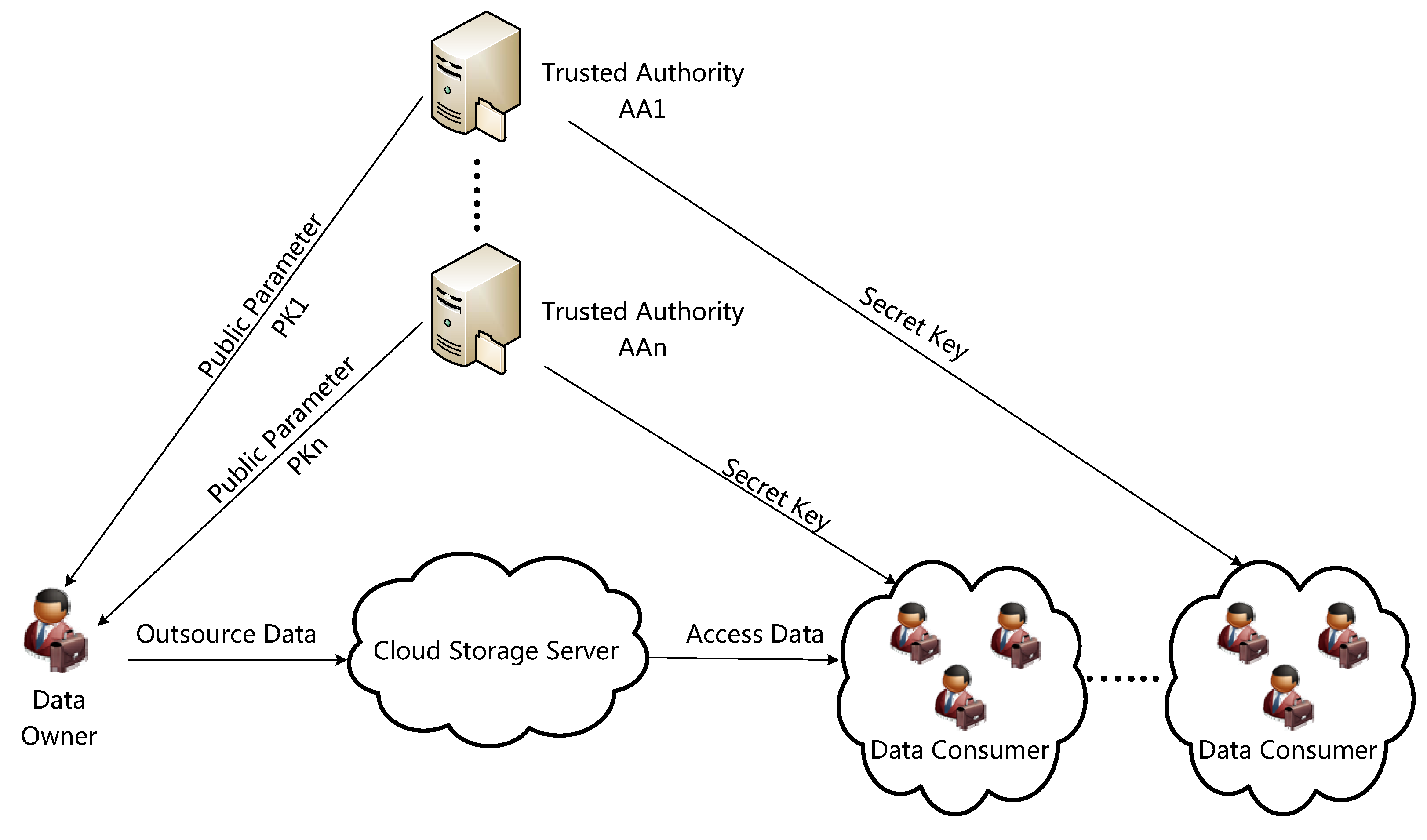
We propose a hierarchical hierarchical user grant filecreation file deletion and attribute-set-based encryption HASBE scheme for access user revocation in cloud computing. By adapting the HABE scheme the performance of public auditing can be improved. Hierarchical attribute-based encryptions Attribute-based signature Cloud computing 1. The traditional encryption schemes such as symmetric and. The proposed scheme inherits flexibility in supporting compound attributes.
 Source: researchgate.net
Source: researchgate.net
In this paper an efficient file hierarchy attribute-based encryption scheme is proposed in cloud computing. In this paper an efficient file hierarchy attribute-based encryption scheme is proposed in cloud computing. The layered access structures are integrated into a single access structure and then the hierarchical files are encrypted with the integrated access structure. HASBE extends the cipher text- prove the security of the proposed scheme based on the policy attribute- set-based encryption CP-ASBE or ASBE. The HABE model which incorporates the property of hierarchical generation of keys in the HIBE system and the property of flexible access control in the CP-ABE system is more applicable to the.
 Source: researchgate.net
Source: researchgate.net
Cloud computing hierarchical attribute-based encryption fine-grained access control scalability 1. Cloud computing is an Internet-based computing pattern through which shared resources are provided to devices on demand. The layered access structures are integrated into a single access structure and then the hierarchical files are encrypted with the integrated access structure. Cloud computing is a revolutionary computing technique by which computing resources are provided dynamically via Internet is widely popular. On outsourced data it provides both efficient and flexible access control in cloud computing.
 Source: researchgate.net
Source: researchgate.net
The ciphertext components related to attributes could be shared by the files. The traditional encryption schemes such as symmetric and. However storing the data in the untrusted cloud server leads the privacy and access control issues in the cloud. Cloud computing is a revolutionary computing technique by which computing resources are provided dynamically via Internet is widely popular. The ciphertext components related to attributes could be shared by the files.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title hierarchical attribute based encryption in cloud computing by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






