Your Allintextusername filetype log images are available in this site. Allintextusername filetype log are a topic that is being searched for and liked by netizens today. You can Find and Download the Allintextusername filetype log files here. Find and Download all royalty-free photos and vectors.
If you’re searching for allintextusername filetype log pictures information related to the allintextusername filetype log keyword, you have come to the right site. Our site frequently gives you suggestions for seeing the maximum quality video and image content, please kindly surf and find more enlightening video articles and images that match your interests.
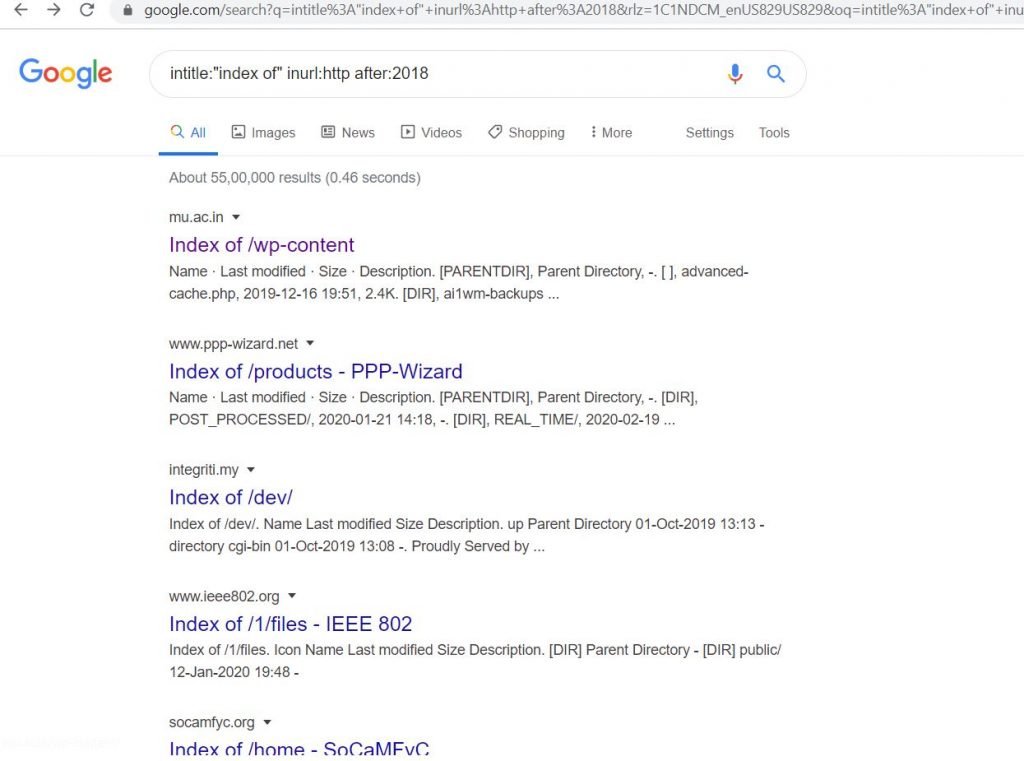
Allintextusername Filetype Log. Allintext Username Filetype log latest news You Google we Google everyone Googles-but is your Googling like maybe. Enter your username or signed up e-mail address and complete the CAPTCHA form. Jinwook Kim On Twitter Google Dork Operator Log Recordsdata Allintext Username Filetype Log 9Invalid character usernamerishey person. Passwordlog filetypelog this keyword is to search for log files in a specific url 22.
 From twitter.com
From twitter.com
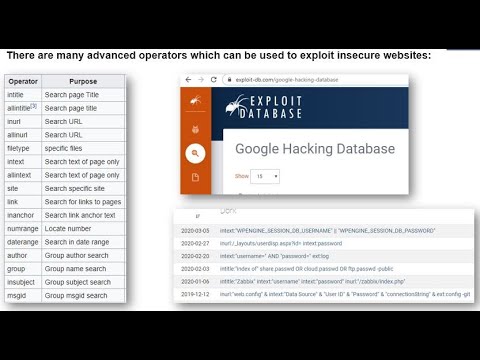
Operators are the foundation of Google geeks. Filetypeeml eml intextSubject intextFrom intextTo filetypefp3 fp3 filetypefp5 fp5 -sitegov -sitemil -cvs log filetypefp7 fp7 filetypeinf inurlcapolicyinf filetypelic lic intextkey filetypelog accesslog -CVS filetypelog cronlog filetypembx mbx intextSubject filetypemyd myd -CVS filetypens1 ns1. Attackers can use this information to log on to that site as that user. It transforms out that Google is great at filling out the blanks so if youre attempting to bear in mind the lyrics to a tune or obtain a list of the important things a famous creator developed simply include an asterisk in the bit of your inquiry you. Reg HKEY_CURRENT_USER username this keyword used to look for reg files registyry to the path HCU Hkey_Current_User In fact there are many more commands that google can crawl in use in the password. Kali Linux OSCP Penetration Testing with Kali Linux PWK PEN-200 All new for 2020 Penetration Testing.
Do not make use of thesaurus words in any language.
LlS log files filetype pst inurl. Google Dorks can be very useful for finding user information posted online. This Google Dork will find logfiles and other things with usernames and passwords posted online. It doesnt work for older rotations of messages eg. Operators are the foundation of Google geeks. Kali Linux OSCP Penetration Testing with Kali Linux PWK PEN-200 All new for 2020 Penetration Testing.
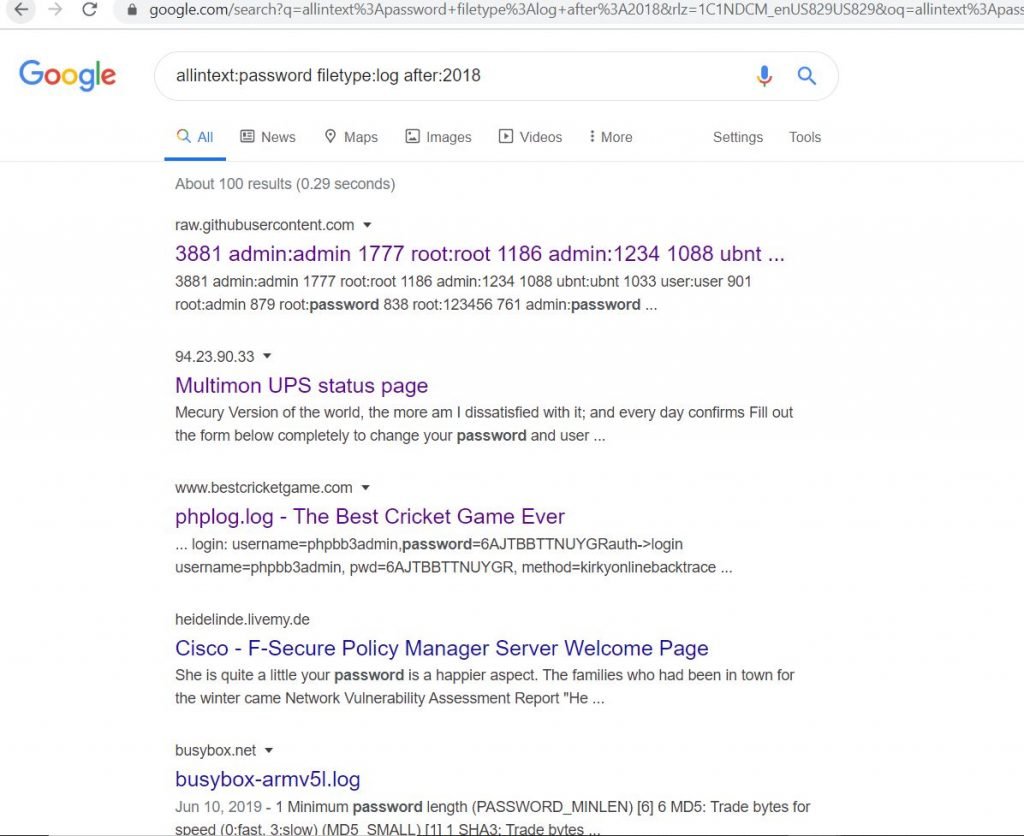 Source: securitynewspaper.com
Source: securitynewspaper.com
Operators are the foundation of Google geeks. 113 lines 89 sloc 297 KB Raw Blame Open with Desktop View raw View blame This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. Allintextusername filetypelog The above command with expose you all the outcomes that features username inside log information. Constructors Log Properties Name. Intrateb tmp PayPallog Go to file Go to file T.
 Source: phoneweek.co.uk
Source: phoneweek.co.uk
Google Dorks can be very useful for finding user information posted online. M db filetype cfm cfapplication title password filetype move move intext useridDescription ASP-Nuke passwords ColdFusion supply with potential passwords dbman credentials allinurlauth person. It doesnt work for older rotations of messages eg. Xpra - screen for X. This will find putty information including server hostnames as well as usernames.
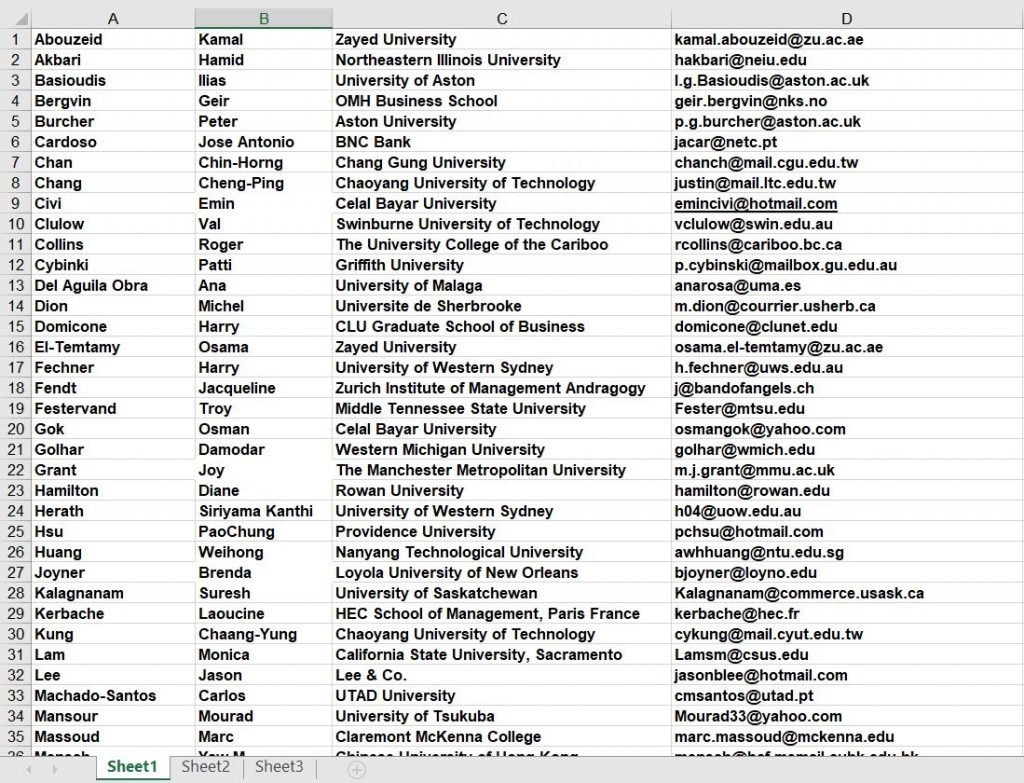 Source: securitynewspaper.com
Source: securitynewspaper.com
Allintext username filetype log netflix. 22012020 You can even use two mixed google operators all in textual. Operators are the foundation of Google geeks. This Google Dork will find logfiles and other things with usernames and passwords posted online. Kali Linux OSCP Penetration Testing with Kali Linux PWK PEN-200 All new for 2020 Penetration Testing.
 Source: lippke.li
Source: lippke.li
Consequently we will certainly address them here first prior to we can create complete dork queries. Cannot retrieve contributors at this time. PCIS Support Team Security. LlS log files filetype pst inurl. Go to line L.
 Source: loginask.com
Source: loginask.com
Copy path Copy permalink. Constructors Log Properties Name. Type Log class inherit MessageContextPropertyBase Public NotInheritable Class Log Inherits MessageContextPropertyBase Inheritance. Jinwook Kim On Twitter Google Dork Operator Log Recordsdata Allintext Username Filetype Log 9Invalid character usernamerishey person. 113 lines 89 sloc 297 KB Raw Blame Open with Desktop View raw View blame This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below.
 Source: stenge.info
Source: stenge.info
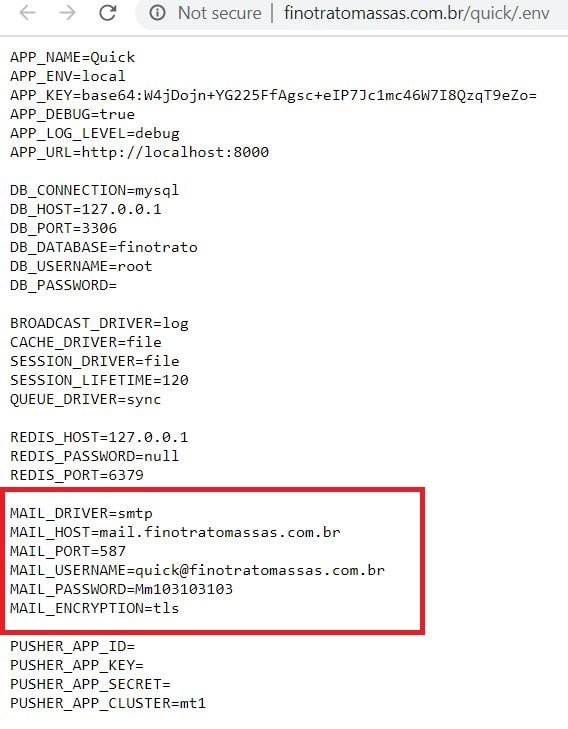
These files contain cleartext usernames and passwords as well as the sites associated with those credentials. An email will be sent to your registered email address with a link. Index of idx_config mailer_password mailer_host mailer_user secret ext. It transforms out that Google is great at filling out the blanks so if youre attempting to bear in mind the lyrics to a tune or obtain a list of the important things a famous creator developed simply include an asterisk in the bit of your inquiry you. Consequently we will certainly address them here first prior to we can create complete dork queries.
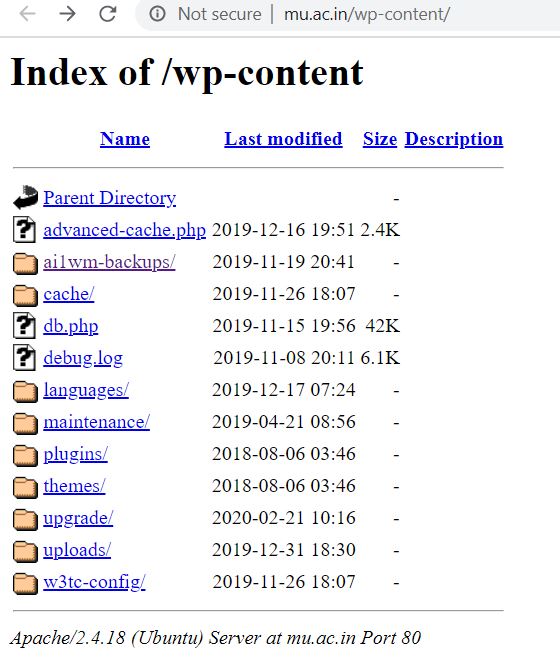 Source: securitynewspaper.com
Source: securitynewspaper.com
This Google Dork will find logfiles and other things with usernames and passwords posted online. 113 lines 89 sloc 297 KB Raw Blame Open with Desktop View raw View blame This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. Reg HKEY_CURRENT_USER username this keyword used to look for reg files registyry to the path HCU Hkey_Current_User In fact there are many more commands that google can crawl in use in the password. Index of idx_config mailer_password mailer_host mailer_user secret ext. Enter your username or signed up e-mail address and complete the CAPTCHA form.
 Source: securitynewspaper.com
Source: securitynewspaper.com
Microsoft FrontPage equivalentof htac- cess shows Web authentication info Microsoft Internet Information Services Internet Information Services. The dork effectively be utilizing to do that is as follows. Allintext Username Filetype log latest news You Google we Google everyone Googles-but is your Googling like maybe. Server refused our key ubuntu109899s password. Intrateb tmp PayPallog Go to file Go to file T.
 Source: twitter.com
Source: twitter.com
Allintext username filetype log netflix. Below is a listing of the most. I love vims colorization of varlogmessages but it only works for that the absolute filename. Reg HKEY_CURRENT_USER username this keyword used to look for reg files registyry to the path HCU Hkey_Current_User In fact there are many more commands that google can crawl in use in the password. 113 lines 89 sloc 297 KB Raw Blame Open with Desktop View raw View blame This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below.
 Source: loginask.com
Source: loginask.com
Google Dorks can be very useful for finding user information posted online. It doesnt work for older rotations of messages eg. 113 lines 89 sloc 297 KB Raw Blame Open with Desktop View raw View blame This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. It transforms out that Google is great at filling out the blanks so if youre attempting to bear in mind the lyrics to a tune or obtain a list of the important things a famous creator developed simply include an asterisk in the bit of your inquiry you. Below is a listing of the most.
 Source: debuglies.com
Source: debuglies.com
Jinwook Kim On Twitter Google Dork Operator Log Recordsdata Allintext Username Filetype Log 9Invalid character usernamerishey person. Operators are the foundation of Google geeks. Reg HKEY_CURRENT_USER username this keyword used to look for reg files registyry to the path HCU Hkey_Current_User In fact there are many more commands that google can crawl in use in the password. Server refused our key ubuntu109899s password. Allintext username filetype log.
 Source: medium.com
Source: medium.com
Google Dorks can be very useful for finding user information posted online. 22062016 intextFill out the shape under utterly to alter your password and person identify. Allintextusername filetypelog The above command with expose you all the outcomes that features username inside log information. Attackers can use this information to log on to that site as that user. This will find putty information including server hostnames as well as usernames.
 Source: loginask.com
Source: loginask.com
An email will be sent to your registered email address with a link. Operators are the foundation of Google geeks. Consequently we will certainly address them here first prior to we can create complete dork queries. Type Log class inherit MessageContextPropertyBase Public NotInheritable Class Log Inherits MessageContextPropertyBase Inheritance. Copy path Copy permalink.
 Source: securitynewspaper.com
Source: securitynewspaper.com
Filetypeeml eml intextSubject intextFrom intextTo filetypefp3 fp3 filetypefp5 fp5 -sitegov -sitemil -cvs log filetypefp7 fp7 filetypeinf inurlcapolicyinf filetypelic lic intextkey filetypelog accesslog -CVS filetypelog cronlog filetypembx mbx intextSubject filetypemyd myd -CVS filetypens1 ns1. LlS log files filetype pst inurl. Xpra - screen for X. Type Log class inherit MessageContextPropertyBase Public NotInheritable Class Log Inherits MessageContextPropertyBase Inheritance. 22062016 intextFill out the shape under utterly to alter your password and person identify.
 Source: resources.infosecinstitute.com
Source: resources.infosecinstitute.com
PCIS Support Team Security. LlS log files filetype pst inurl. Do not make use of thesaurus words in any language. Allintextusername filetypelog The above command with expose you all the outcomes that features username inside log information. Trying to find LOG information will permit us to search for clues about what the credentials to the system or varied consumer or admin accounts could be.
 Source: twitter.com
Source: twitter.com
Outlookpst intitle indexof mt-db-passcgi filetype ctt ctt messenger This file was generated by Nessus inurl. Reg HKEY_CURRENT_USER username this keyword used to look for reg files registyry to the path HCU Hkey_Current_User In fact there are many more commands that google can crawl in use in the password. Allintext Username Filetype log latest news You Google we Google everyone Googles-but is your Googling like maybe. 22012020 You can even use two mixed google operators all in textual. Attackers can use this information to log on to that site as that user.
 Source: phoneweek.co.uk
Source: phoneweek.co.uk
Consequently we will certainly address them here first prior to we can create complete dork queries. One who has the ability google reveals in this case is. Allintext Username Filetype log latest news You Google we Google everyone Googles-but is your Googling like maybe. Server refused our key ubuntu109899s password. 22062016 intextFill out the shape under utterly to alter your password and person identify.
 Source: twitter.com
Source: twitter.com
Kali Linux OSCP Penetration Testing with Kali Linux PWK PEN-200 All new for 2020 Penetration Testing. Intrateb tmp PayPallog Go to file Go to file T. Server refused our key ubuntu109899s password. Copy path Copy permalink. Filetypeeml eml intextSubject intextFrom intextTo filetypefp3 fp3 filetypefp5 fp5 -sitegov -sitemil -cvs log filetypefp7 fp7 filetypeinf inurlcapolicyinf filetypelic lic intextkey filetypelog accesslog -CVS filetypelog cronlog filetypembx mbx intextSubject filetypemyd myd -CVS filetypens1 ns1.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title allintextusername filetype log by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






